8. Prepare for Cloud Security
Overview
https://learn.microsoft.com/en-us/training/modules/cloud-adoption-framework-security/
Pretend that your Organization is moving toward this framework.
Your leadership wants to implement:
- Tools
- Controls
- Architectures
- Security operations
- Administration practices
Which will:
- Reduce risk from major incidents: The CISO wants to prevent as many incidents as possible, limit the damage from successful attacks, and rapidly detect, respond to, and recover from incidents. She also wants to be able to restore business processes without paying a ransom.
- Identify and protect sensitive business data: The CISO wants to clearly identify what business assets are important to the organization and map those assets into technical assets. She also wants to protect those assets appropriately whether they're structured data, unstructured data, or any types of applications or systems that enable business-critical processes.
- Rapidly modernize the existing security program: The CISO wants to modernize the security program with well-planned initiatives that prioritize quick wins and incremental progress across all security disciplines.
- Show the company has a strong security posture to build confidence with employees, partners, customers, and stakeholders: The CISO wants to provide the right level of details on Tailwind Traders' security posture to organization leadership, oversight, and business partners. She wants to carefully balance the ability to provide enough information to build trust while limiting risk from disclosing too much data.
- Proactively meet regulatory and compliance requirements: The CISO wants to rapidly discover, understand, meet, and report compliance with external requirements.
- Reduce the cost and complexity of doing business: The CISO wants to simplify security processes and reduce friction in business processes from security. Modernizing workloads and applying modern security intelligence, automation, monitoring, and defense approaches is key to this effort.
Security
- Risk insights: Align and integrate security insights and risk signals and sources to the business initiatives. Ensure repeatable processes educate all teams on the application of those insights and hold teams accountable for improvements.
- Security integration: Integrate security knowledge, skills, and insights deeper into daily business operations and IT environment. Use repeatable processes and develop a deep partnership at all levels of the organization.
- Business resilience: Prevent as many attacks as possible and limit the damage of those attacks to foster organizational resilience. Ensure that you can continue operations during an attack, even if at a degraded state. Also ensure the organization rapidly bounces back to full operations.
Security Disciplines
- Access control: Apply network and identity create access boundaries and segmentation to reduce the frequency and reach of any security breaches.
- Security operations: Monitor IT operations to detect, respond, and recover from a breach. Use data to continuously reduce risk of breach.
- Asset protection: Maximize protection of infrastructure, devices, data, applications, networks, and identities to minimize risk to the overall environment.
- Security governance: Monitor decisions, configurations, and data to govern decisions made across the environment and within all workloads across the portfolio.
- Innovation security: Integrate security into your DevOps models to improve security and safety assurances as you increase the pace of innovation in your organization. To avoid expensive security incidents and late-stage mitigation, security must become an integral part of a DevSecOps process. Empower workload teams to quickly identify and mitigate security risks.
Responsibilities
- Policy and standards
- Security operations
- Security architecture
- Security compliance management
- People security
- Application security and DevSecOps
- Data security
- Infrastructure and endpoint security
- Identity and key management
- Threat intelligence
- Posture management
- Incident preparation
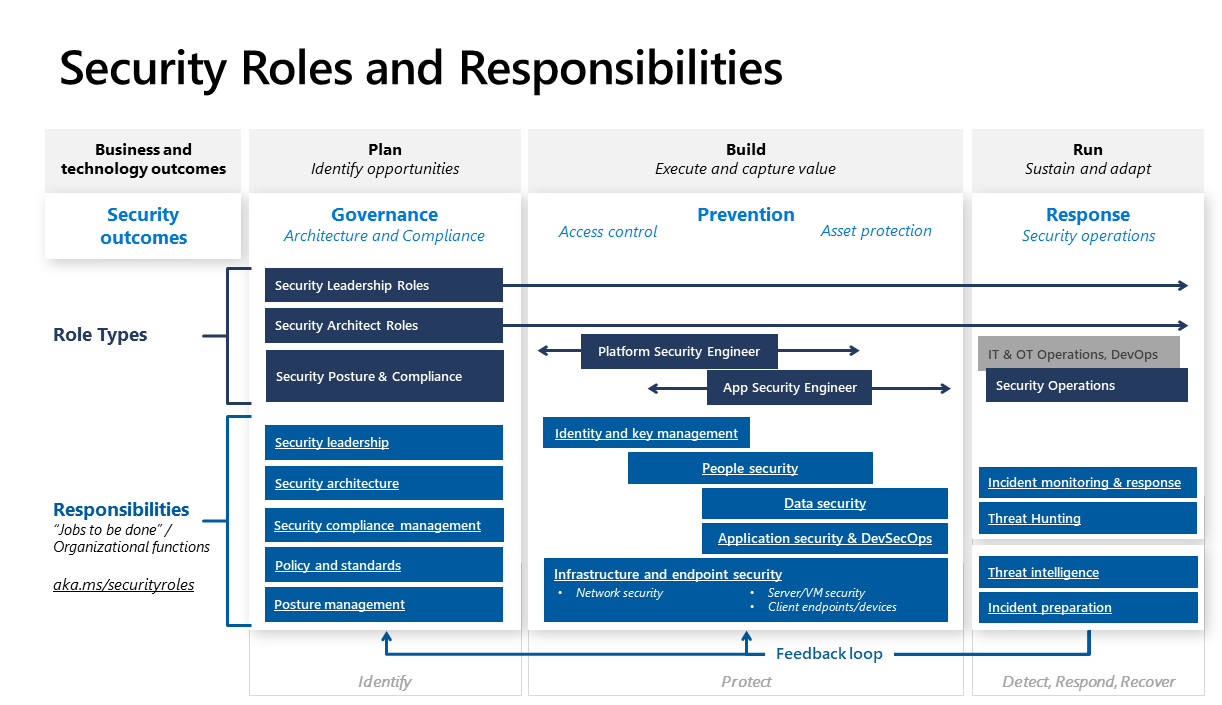
Role Types
https://www.youtube.com/watch?v=GlqjvlX93gY&list=PLtVMyW0H7aiOQwZSsn2d-tg2z729ce1BZ&index=13
- Security leadership: These roles frequently span across functions. They ensure that teams coordinate with each other, prioritize, and set cultural norms, policies, and standards for security.
- Security architect: These roles span across functions and provide a key governance capability to ensure all the technical functions work harmoniously within a consistent architecture.
- Security posture and compliance: This newer role type represents the increasing convergence of compliance reporting with traditional security disciplines like vulnerability management and configuration baselines. While the scope and audience are different for security and compliance reporting, they answer different versions of the question "How secure is the organization?" The way that question is answered is growing more similar via tools like Microsoft Secure Score and Microsoft Defender for Cloud.
- The use of on-demand data feeds from cloud services reduces the time required to report compliance.
- The increased scope of data available enables security governance to look beyond traditional software updates or patches and discover and track "vulnerabilities" from security configurations and operational practices.
- Platform security engineer: These technology roles focus on platforms that host multiple workloads focused on access control and asset protection. These roles are often grouped into teams with specialized technical skill sets. They include network security, infrastructure and endpoints, and identity and key management. These teams work on preventive controls and detective controls, with detective controls being a partnership with SecOps and preventive controls being primarily a partnership with IT operations. For more information, see Security integration.
- Application security engineer: These technology roles focus on security controls for specific workloads and support classic development models and modern DevOps/DevSecOps models. They blend application and development security skills for unique code and infrastructure skills for common technical components like VMs, databases, and containers. These roles might be in central IT or security organizations, or within business and development teams based on organizational factors.
Security Benchmarks
The Azure Security Benchmark documentation specifies security controls and service recommendations:
- Security controls: The Azure Security Benchmark recommendations are categorized by security controls. Security controls represent high-level, vendor-agnostic security requirements, like network security and data protection. Each security control has a set of security recommendations and instructions that help you implement those recommendations.
- Security baselines: When available, benchmark recommendations for Azure services include the Azure Security Benchmark recommendations that are tailored specifically for that service.
Implement the Azure Security Benchmark in three steps:
- Plan your implementation: Review the documentation for the enterprise controls and service-specific baselines. Plan your control framework and how it maps to guidance like CIS controls, NIST, and the PCI Data Security Standard framework.
- Monitor your compliance: Use the Microsoft Defender for Cloud regulatory compliance dashboard to monitor compliance with the Azure Security Benchmark status and other control sets.
- Establish guardrails: Automate secure configurations and enforce compliance with the Azure Security Benchmark and other requirements in your organization with Azure Policy.
Landing Zones
Azure landing zones are a logical construct that captures everything that must be true to enable application migrations and development at scale in Azure. Landing zones consider all platform resources that are required to support your organization's application portfolio. Azure landing zones provide cloud adoption teams with a well-managed environment for their workloads.
https://learn.microsoft.com/en-us/azure/cloud-adoption-framework/ready/
Best Practices
- Establish essential security practices.
- Modernize the security strategy.
- Develop a security plan.
- Secure new workloads.
- Secure existing cloud workloads.
- Govern to manage and improve security posture.
https://learn.microsoft.com/en-us/training/paths/enterprise-scale-architecture/
Tools
- Microsoft Defender for Cloud: Provides the tools needed to harden your resources, track your security posture, protect against cyberattacks, and streamline security management.
- Microsoft Entra ID: The default identity and access management service. Microsoft Entra ID provides an identity security score to help you assess your identity security posture relative to Microsoft's recommendations.
- Microsoft Sentinel: A cloud-native SIEM that provides intelligent security analytics for your entire enterprise, powered by AI.
- Azure Distributed Denial of Service (DDoS) standard protection plan (optional): Provides enhanced DDoS mitigation features to defend against DDoS attacks.
- Azure Firewall: A cloud-native and intelligent network firewall security service that provides threat protection for your cloud workloads running in Azure.
- Web Application Firewall: A cloud-native service that protects web apps from common web-hacking techniques such as SQL injection and security vulnerabilities such as cross-site scripting.
- Privileged Identity Management (PIM): A service in Microsoft Entra ID that lets you manage, control, and monitor access to important resources in your organization.
- Microsoft Intune: A cloud-based service that focuses on mobile device management and mobile application management.
Baseline implementation
After the right tools are in place, make sure you have good policies in place to enforce proper use of those tools. Several policies apply to online and corporate-connected landing zones:
- Enforce secure access, like HTTPS, to storage accounts: Configure your storage account to accept requests from secure connections only by setting the Secure transfer required property for the storage account. When you require secure transfer, any requests that originate from an insecure connection are rejected.
- Enforce auditing for Azure SQL Database: Track database events and write them to an audit log in your Azure storage account, Log Analytics workspace, or event hubs.
- Enforce encryption for Azure SQL Database: Transparent data encryption helps protect SQL Database, Azure SQL Managed Instance, and Azure Synapse Analytics against the threat of malicious offline activity by encrypting data at rest.
- Prevent IP forwarding: IP forwarding enables a network interface attached to a VM to receive network traffic not destined for any of the IP addresses assigned to any of the network interface's IP configurations. You can also send network traffic with a different source IP address than the one assigned to one of a network interface's IP configurations. The setting must be enabled for every network interface that's attached to the VM that receives traffic that the VM needs to forward.
- Ensure subnets are associated with network security groups (NSGs): Use an Azure NSG to filter network traffic to and from Azure resources in an Azure virtual network. An NSG contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources. For each rule, you can specify the source and destination, port, and protocol.
Summary
- Understand the cloud security methodology.
- Identify security roles and responsibilities.
- Assess cultural and role and responsibility changes that typically come with cloud adoption.
- Learn how to simplify compliance and security implementation in the cloud